How to Mitigate Ransomware Threats with Microsoft Security Tools

Ransomware poses a significant threat to businesses today. You face potential financial losses ranging from $350,000 to $1.4 million if you fall victim to these attacks. The average cost of a ransomware incident can reach $4.62 million, according to IBM. These figures highlight the urgent need for robust security measures. Using security tools becomes crucial in safeguarding your data and operations. Microsoft Security Tools offer effective solutions to help you Mitigate Ransomware Threats. By implementing these tools, you can protect your business from devastating attacks and ensure continuity.
Understanding Ransomware
Definition of Ransomware
What is Ransomware?
Ransomware is a type of malicious software that encrypts your files, making them inaccessible. Attackers demand a ransom to restore access. This threat can disrupt your business operations and lead to significant financial losses.
How Ransomware Works
Ransomware typically infiltrates your system through phishing emails or malicious downloads. Once inside, it encrypts your data and displays a ransom note. You must act quickly to prevent further damage.
Types of Ransomware
Crypto Ransomware
Crypto ransomware encrypts your files, rendering them unusable. You need a decryption key, which attackers offer in exchange for payment. This type poses a severe risk to your data integrity.
Locker Ransomware
Locker ransomware locks you out of your device entirely. Unlike crypto ransomware, it doesn't encrypt files but prevents access to your system. You face pressure to pay the ransom to regain control.
Scareware
Scareware tricks you into believing your computer is infected with a virus. It demands payment for fake antivirus software. Though less harmful, it can still cause panic and unnecessary expenses.
Key Insight: According to a study by Cybereason, two-thirds of businesses experience significant revenue loss after a ransomware attack. Understanding these types helps you prepare and protect your organization effectively.
The Importance of Ransomware Prevention
Impact of Ransomware Attacks
Financial Losses
Ransomware attacks can lead to severe financial losses. When attackers encrypt your files, they demand a ransom for the decryption key. Paying this ransom does not guarantee file recovery. You might also face additional costs for system restoration and data recovery. Businesses often experience revenue loss due to operational downtime. According to Cybereason, two-thirds of businesses report significant revenue loss after a ransomware attack. You must consider these potential financial impacts when evaluating your cybersecurity strategy.
Data Breaches
Ransomware attacks can result in data breaches. Attackers may access sensitive information during the encryption process. This breach can compromise customer data, leading to legal consequences and reputational damage. You risk losing customer trust if their data is exposed. Protecting your data from unauthorized access is crucial to maintaining your business's integrity and reputation.
Benefits of Prevention
Cost Savings
Preventing ransomware attacks can save you money. Investing in security tools and training is more cost-effective than dealing with an attack's aftermath. According to industry experts, prevention measures cost significantly less than recovery efforts. By implementing robust security protocols, you reduce the likelihood of paying ransoms or facing costly data recovery processes.
Enhanced Security
Prevention enhances your overall security posture. By using tools like Microsoft Security Suite, you can detect threats in real-time and respond swiftly. These tools offer features such as automated responses and threat scanning, which help protect your systems. Regular updates and employee training further strengthen your defenses. A proactive approach to security not only mitigates ransomware risks but also safeguards against other cyber threats.
Introduction to Microsoft Security Tools
Overview of Microsoft Security Suite
Microsoft offers a comprehensive suite of security tools designed to protect your business from ransomware threats. Two key components of this suite are Microsoft Defender and Azure Security Center.
Microsoft Defender
Microsoft Defender provides robust protection against ransomware and other cyber threats. It offers real-time threat detection, helping you identify and neutralize potential risks before they cause harm. With its automated response capabilities, Microsoft Defender can take immediate action to quarantine and remove malicious software. This proactive approach ensures that your systems remain secure and operational.
Azure Security Center
Azure Security Center enhances your security posture by providing advanced threat protection for your cloud resources. It continuously monitors your environment, identifying vulnerabilities and recommending best practices to mitigate risks. By customizing security policies, you can tailor the protection to meet your specific needs. Azure Security Center also offers real-time monitoring and incident response, enabling you to swiftly address any security incidents.
Key Features of Microsoft Security Tools
Microsoft Security Tools come equipped with several key features that enhance your ability to combat ransomware threats.
Real-time Threat Detection
Real-time threat detection is a crucial feature of Microsoft Security Tools. It allows you to monitor your systems continuously, identifying potential threats as they arise. This capability enables you to respond quickly, minimizing the impact of any security incidents. By staying vigilant, you can prevent ransomware from infiltrating your systems and causing damage.
Automated Response
Automated response is another vital feature that helps you mitigate ransomware threats effectively. When a threat is detected, Microsoft Security Tools can automatically take action to neutralize it. This includes quarantining infected files and removing malicious software. By automating these processes, you reduce the risk of human error and ensure a swift response to any security incidents. This proactive approach helps maintain the integrity and security of your systems.
Product Information: Utilizing tools like Microsoft Defender and Azure Security Center can save you significant costs associated with recovering from a ransomware attack. Prevention is always more cost-effective than dealing with the aftermath of an infection.
How to Use Microsoft Defender to Mitigate Ransomware Threats
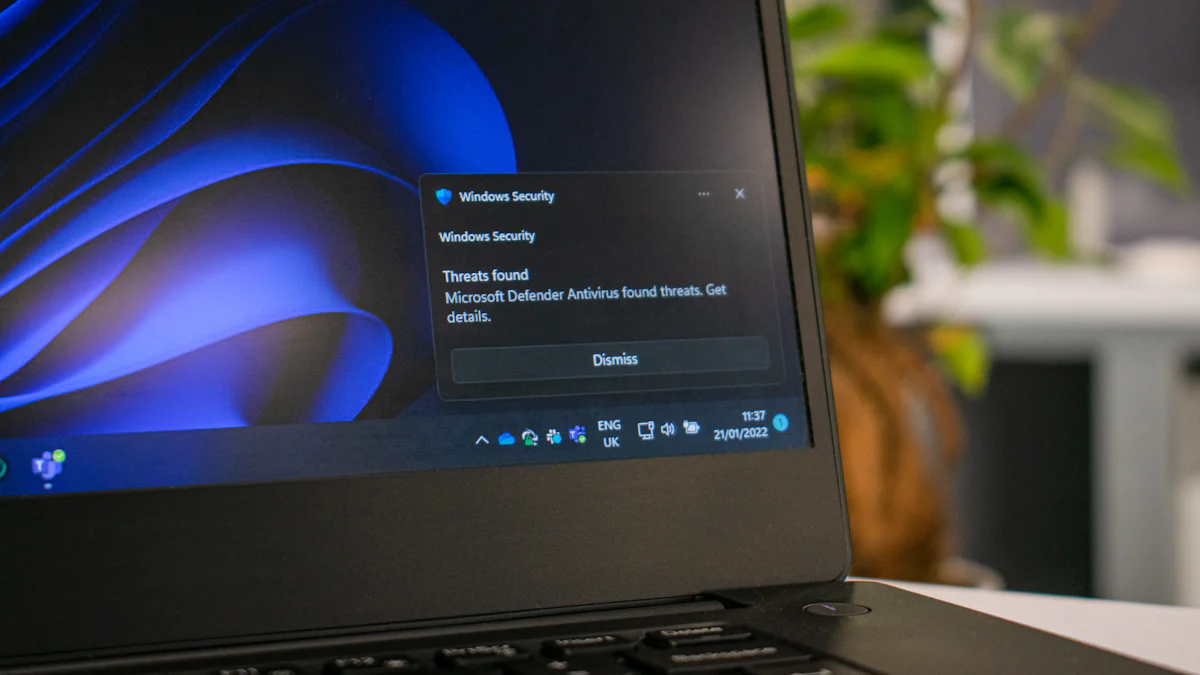
Setting Up Microsoft Defender
Installation Process
To start using Microsoft Defender, you need to install it on your system. First, ensure your operating system is up to date. This step is crucial for compatibility and security. Next, navigate to the Microsoft Store or official website to download Microsoft Defender. Follow the on-screen instructions to complete the installation. The process is straightforward and user-friendly, allowing you to quickly set up protection against ransomware.
Configuration Settings
After installation, configure Microsoft Defender to suit your needs. Open the application and access the settings menu. Here, you can customize various options. Enable real-time protection to monitor threats continuously. Adjust the scan frequency to ensure regular checks of your system. You can also set up notifications to alert you of any detected threats. Proper configuration enhances your ability to mitigate ransomware threats effectively.
Utilizing Microsoft Defender Features
Threat Scanning
Microsoft Defender offers robust threat scanning capabilities. To perform a scan, open the application and select the scan option. Choose between a quick scan for immediate threats or a full scan for a comprehensive check. The software will examine your files and system for any signs of ransomware. Regular scans help you identify and address potential risks before they escalate.
Quarantine and Removal
When Microsoft Defender detects a threat, it automatically quarantines the malicious files. This action prevents the ransomware from spreading further. You can review the quarantined items in the application. If confirmed as threats, proceed to remove them permanently. This feature ensures that your system remains clean and secure. By actively managing detected threats, you maintain control over your cybersecurity environment.
Leveraging Azure Security Center for Ransomware Protection

Setting Up Azure Security Center
Initial Setup
To begin using Azure Security Center, you first need to set it up. Start by accessing the Azure portal. Once there, locate the Security Center option in the menu. Click on it to initiate the setup process. You will need to enable the Security Center for your subscription. This step allows you to monitor and protect your resources effectively. Follow the on-screen instructions to complete the initial setup. The process is straightforward, ensuring you can quickly start securing your environment.
Customizing Security Policies
After the initial setup, customize your security policies. Open the Security Center dashboard and navigate to the policy management section. Here, you can tailor the security settings to meet your specific needs. Adjust the policies to focus on ransomware protection. Enable features like threat detection and vulnerability assessment. These settings help you identify and mitigate potential risks. By customizing your security policies, you enhance your defense against ransomware attacks.
Monitoring and Responding to Threats
Real-time Monitoring
Azure Security Center offers real-time monitoring capabilities. This feature allows you to keep an eye on your cloud resources continuously. Access the Security Center dashboard to view the real-time monitoring section. Here, you can see alerts and notifications about potential threats. The system analyzes your environment for any suspicious activities. By staying vigilant, you can detect ransomware attempts early. Real-time monitoring helps you respond swiftly, minimizing the impact of any security incidents.
Incident Response
When a threat is detected, you must act quickly. Azure Security Center provides tools for effective incident response. Access the incident response section in the dashboard. Review the alerts and prioritize them based on severity. For each alert, follow the recommended actions to neutralize the threat. This may include isolating affected resources or applying security patches. By responding promptly, you prevent ransomware from spreading further. An effective incident response plan ensures your systems remain secure and operational.
Key Insight: According to Cybereason's study, early detection and response are crucial in minimizing the damage caused by ransomware. By leveraging tools like Azure Security Center, you can protect your business from significant financial losses and reputational damage.
Implementing Best Practices for Ransomware Prevention
Regular Software Updates
Importance of Updates
You must keep your software up to date to protect against ransomware. Updates often include security patches that fix vulnerabilities. Without these patches, your system becomes an easy target for attackers. Regular updates ensure that your defenses remain strong and effective.
Automating Updates
Automating updates simplifies the process and ensures consistency. By enabling automatic updates, you reduce the risk of missing critical patches. This proactive approach keeps your system secure without requiring constant manual intervention.
Employee Training and Awareness
Conducting Training Sessions
Training your employees is crucial in preventing ransomware attacks. You should organize regular training sessions to educate them about the latest threats. These sessions help employees recognize suspicious activities and respond appropriately.
Phishing Simulations
Phishing simulations provide practical experience in identifying threats. By conducting these exercises, you can test your employees' awareness and improve their skills. Simulations prepare them to handle real-world scenarios, reducing the risk of successful attacks.
Cybereason Experts emphasize that prevention costs significantly less than recovery. Investing in these best practices can save you from the high costs of a ransomware infection.
Post-Attack Actions and Recovery
Steps to Take After a Ransomware Attack
Isolating Infected Systems
You must act quickly to isolate infected systems. Disconnect affected devices from the network to prevent the ransomware from spreading. This step helps contain the threat and protects other parts of your infrastructure. Ensure that you identify all compromised systems to effectively halt the attack.
Contacting Authorities
Contact local authorities immediately after isolating the threat. Reporting the incident can help in tracking down the attackers and may provide you with additional resources. Authorities can offer guidance on legal obligations and assist in the investigation process. This collaboration is crucial for a comprehensive response.
Recovery and Restoration
Data Backup and Restoration
Having a reliable data backup is essential. Regularly back up your data to ensure you can restore it after an attack. Use cloud-based solutions or external drives for secure storage. Once you have isolated the threat, begin restoring your data from these backups. This process helps you regain access to critical information without paying a ransom.
System Rebuilding
Rebuilding your systems is a vital step in recovery. Start by wiping infected devices to remove any lingering threats. Reinstall operating systems and applications from trusted sources. Ensure that you apply all security patches and updates during this process. This approach not only restores functionality but also strengthens your defenses against future attacks.
Key Insight: According to industry reports, ransomware attacks can lead to significant revenue loss and damage to your brand. By following these recovery steps, you can minimize the impact and protect your business's reputation.
Using Microsoft Security Tools is crucial in protecting your business from ransomware threats. These tools offer robust features like real-time threat detection and automated responses, ensuring your systems remain secure. Implementing the strategies discussed can significantly enhance your protection.
Survey Insight: Two-thirds of businesses experience revenue loss after a ransomware attack. Protecting your brand and reputation is vital. By adopting these measures, you safeguard your operations and maintain trust with your clients. Prioritize security to prevent costly disruptions and potential loss of key personnel.
See Also
Securing Your Microsoft Setup with Azure Security Center
Top Security Practices for IT Admins in Microsoft Azure
Mastering Microsoft Security Solutions
Enhancing Corporate Device Security with Microsoft Intune
Getting Started with Microsoft Defender for Endpoint Protection
